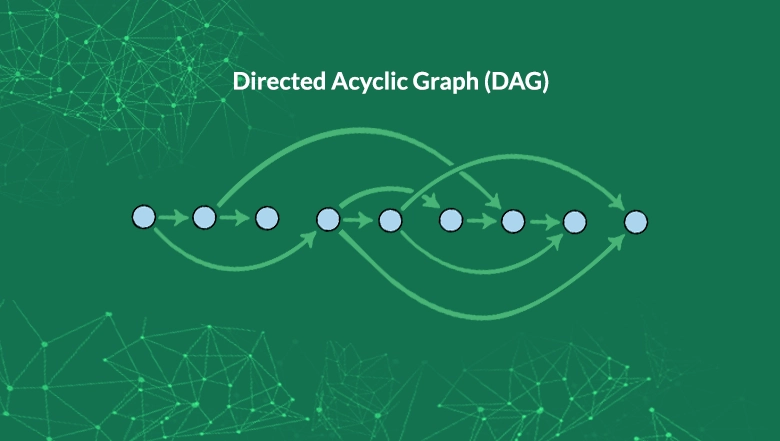
What a DAG?
Directed Acyclic Graph (DAG) uses topological ordering for a directed graphical structure. The sequence can move from earlier to later. DAG can be applied to issues related to data processing, scheduling of projects, Shortest path problems, and data compression. The sequence is maintained by the involvement of transactions, thus skipping the process of mining. DAG’s blockless design consists of only transactions, eliminating the need for miners to create new blocks.
In addition, DAG allows users to secure data by referencing data units from previous transactions, thereby increasing the scalability of transactions. The consensus algorithm establishes total order in the DAG by selecting the ‘main chain’ that gravitates towards reputable users, aka witnesses.
Benefits
No Double Spending
The validation of a transaction is decided by the transactions behind it. DAG’s transaction order is expanded through multiple transactions, without a Proof of Work (PoW). Any attempts of double spending will be thwarted immediately by the system.
Network Width
The DAG network link the existing later transactions to the new transactions. The DAG algorithm will control the width of the tangled network. When the transactions are validated, it will be linked to new transactions on the DAG network.
Faster Transactions
The blockless nature of the DAG makes the transactions run directly into the network, which makes the whole process faster than PoW & PoS. The network width is kept within certain limits to maintain faster transaction validation.
Micro-Transactions
The advent of DAG has enabled a platform, where there is a possibility of high functioning with a minimal transaction fee. Users can send and receive micro and nano-payments without issues related to scalability and transactional speed.
Features

Conditional Payments
DAG allows the payer to set conditional payments that fiat currency transactions cannot. The conditions are set by the payer. The payee receives the money, only when these conditions are met or else the money is returned to the payer.

Sovereign Identity
The identity of the user is stored securely on the wallet. The disclosure of the identity is up to the user. The user can disclose the wallet identity to a service provider, for example, participation in an ICO, and use the wallet identity as part of their KYC & AML compliance.

Privacy
Users can pay in complete privacy in a cash-like currency that is untraceable. The transactions will not be visible on the public database, as they are sent Peer-to-Peer (P2P). The built-in TOR switch enables direct transfer from wallet to wallet, further increasing privacy.

Secure Transactions
DAG does not have a central entity that stores and process payments. Instead, when the transactions between users are initiated, a cryptographic link is created between each other. As the transactions grow, users start adding their link on top of each other like Byteball.
Use Cases

ICO Differentiation
When the ICOs are run on the blockchain, cryptocurrency on DAG can be out of the box security tokens. The KYC is built-in with real name verifications with stats that are displayed in real time. Users sell BTC, ETH, or Bytes.

Peer-to-Peer Insurance
The user can hedge the insurance against any negative events. Insurance is inscribed on a smart contract, which will be unlocked by the insured when the event in question occurs. The user can also sell insurance for a profit in a P2P transaction.

Peer-to-Peer Prediction
Users can predict a future event and can make money. It could be betting on a football match or any other prediction market. The prediction will be etched on a smart contract and depending on the result, the user or the peer can unlock the smart contract.

Email or Chat Trade
The payer can send the cryptocurrency through e-mail or via chat. The recipient can click the link received by mail or chat to complete the transaction. However, if the recipient does not have a DAG wallet, the link will prompt them to install a wallet on Android or iOS.